Following helpbook contains information about scams identified by Laser Desk.
We explain how they work (mechanics), how to detect them (identification), and what to do if you're a victim (mitigation).
For any feedback & suggestions — @Laser_Desk
Examples of past scams: milkyswap.io, rocketboys.io, alpinecars.io, stakedao.online, dex88.org, swap8.io, artificial reality token, Phoenix, Pegasus Network,
Mechanics
The idea is to trick you to interact (buy / sell / swap / transfer) with some malicious token or website:
-
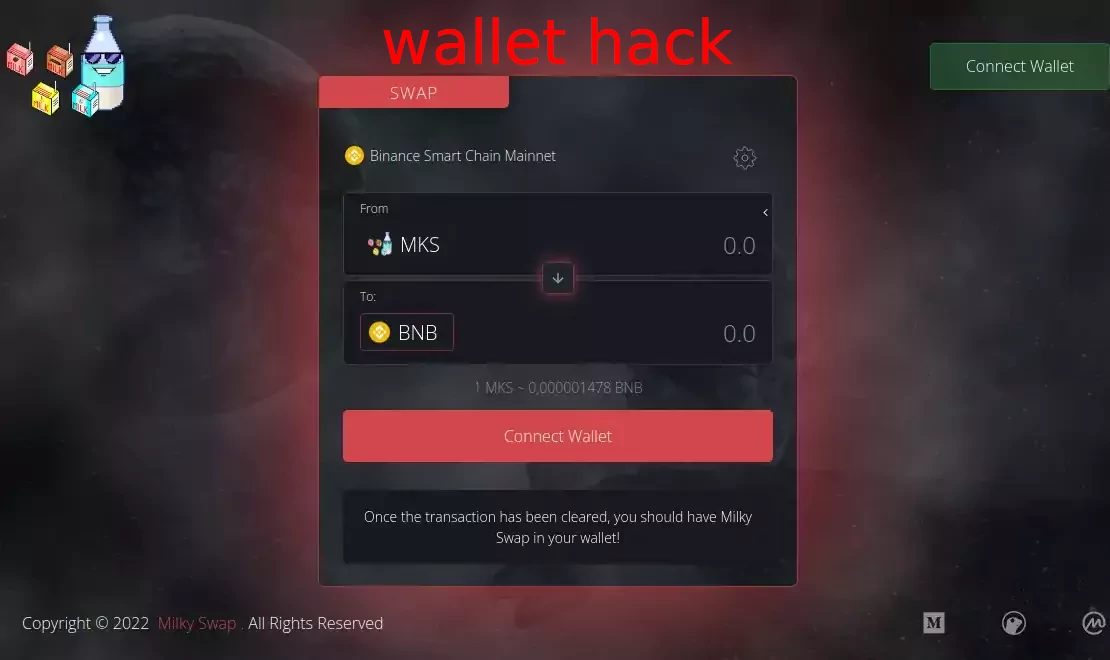
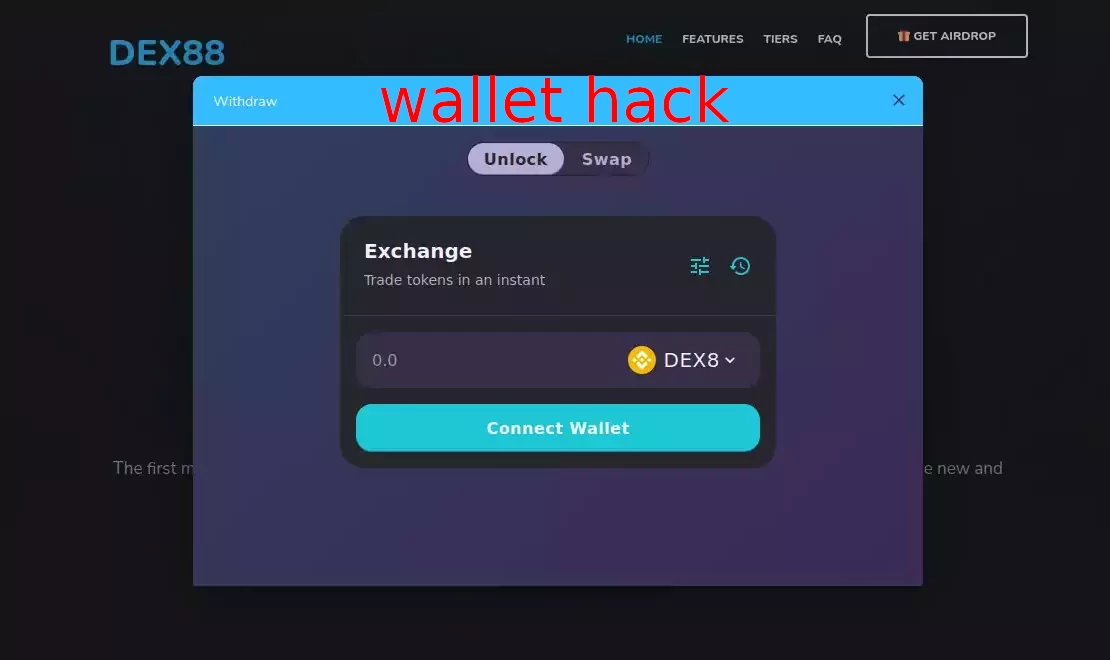
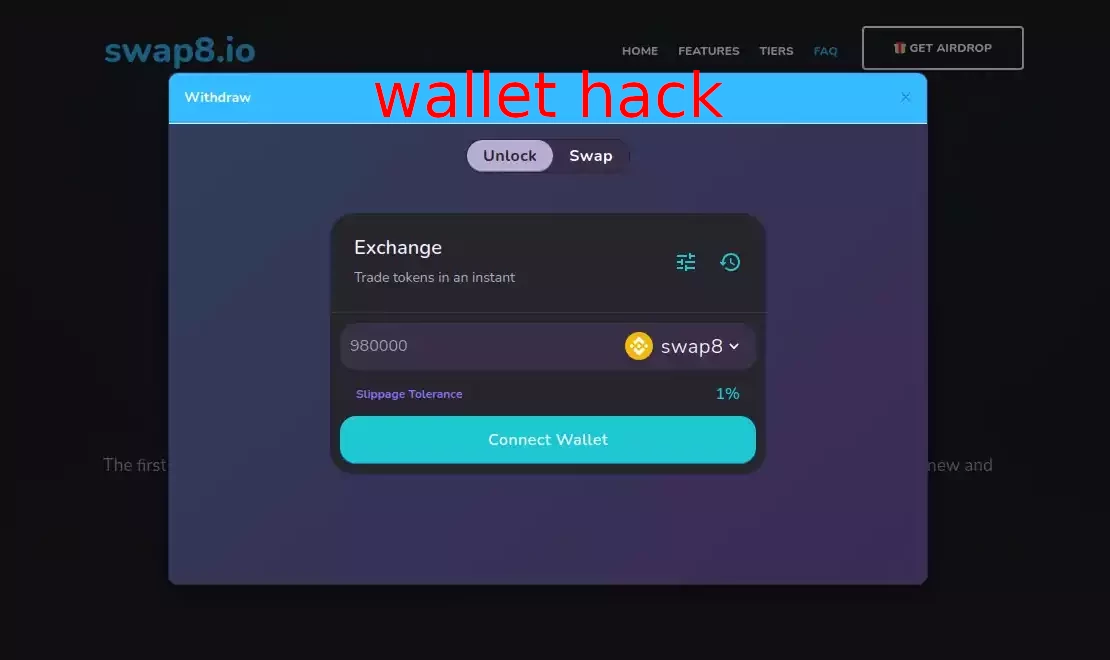
wallet hack scam —
- scam token is airdropped to multiple wallets
- token is either malicious itself or leads to a malicious website (e.g. token has name 'usdswap.io')
- when you try to interact with it — your wallet gets compromised (you either approve unlimited access to your tokens or leak your secret recovery phrase)
- scammer steals tokens from your wallet
-
hidden fee scam —
- scam token is airdropped to multiple wallets
- when you try to swap / transfer token you pay an extreme hidden transaction fee
- scammer collects these fees
-
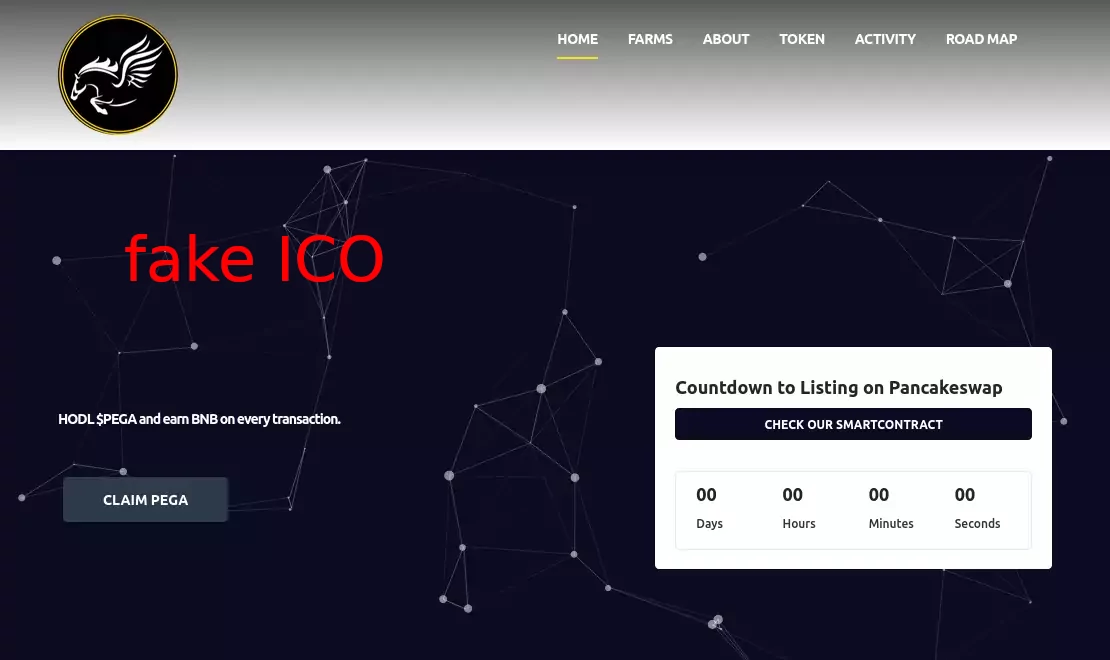
fake ICO scam (presale rug) —
- scammer creates a fake project and starts marketing ICO (Initial Coin Offering or just presale)
- you participate in ICO and buy token
- when ICO ends — nothing happens, scammer just disappers with your money
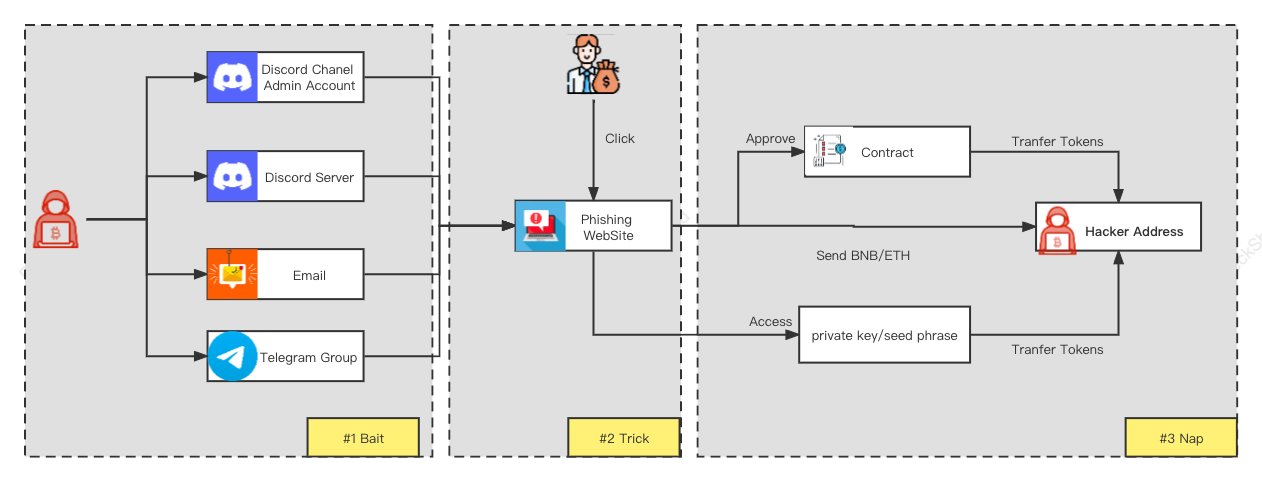
Illustration by PeckShield
Less common goals may include directing you to a phishing or a malware website or performing a dusting attack.
Indentification
Phishing tokens:
- always are too good to be true: no one gives a lot of money for free, even in crypto
- always force you to do something: to swap a token, to get an airdrop, to grant some permissions, to send some information, etc.
- often are anonymous: no team, no CEX listings, no audit, no meaningful project description, no active / moderated social accounts
- often are generous and unconditional: while legit airdrops (e.g. from CoinMarketCap list) distribute small prize pool in a lottery and require you to do some tasks to win — scams give airdrops to everyone and for nothing
- often have unverified contract source code: scammers don't want anyone to know their intentions
- usually are airdropped to a huge number of wallets: if you've suddenly received a young unknown token with 10000+ holders — it's a scam in 100% cases
Articles:
- LSR.Finance: Airdrop crypto scams: yetiswap.io, milkyswap.io, mmdex.io, artificial reality token and other (Reddit link), Medium link
- Hackernoon: How To Spot Scammy Token Sales
- Investopedia: How to Identify Cryptocurrency and ICO Scams
Mitigation
Your best strategy is to ignore the airdropped token:
- don't try to buy / sell / swap / transfer it
- don't grant ANY permissions to your wallet
- don't visit suspicious websites and click untrusted links
If you see an unknown token in your wallet — hide it (metamask, trustwallet).
If you've unintentionally granted permissions — revoke them (via BscScan, allowance.beefy.finance, revoke.cash or other tools).
If your seed phrase or private key has been compromised — immediately create completely new (uncompromised) wallet and transfer all your tokens there.
If you want to avoid phishing websites — install PeckShield chrome extension.
Examples of past scams: Forta, Mark Meta, Wolfi, Ape of Arena, Happy Valentine 2022, Meta Dragon City
Mechanics
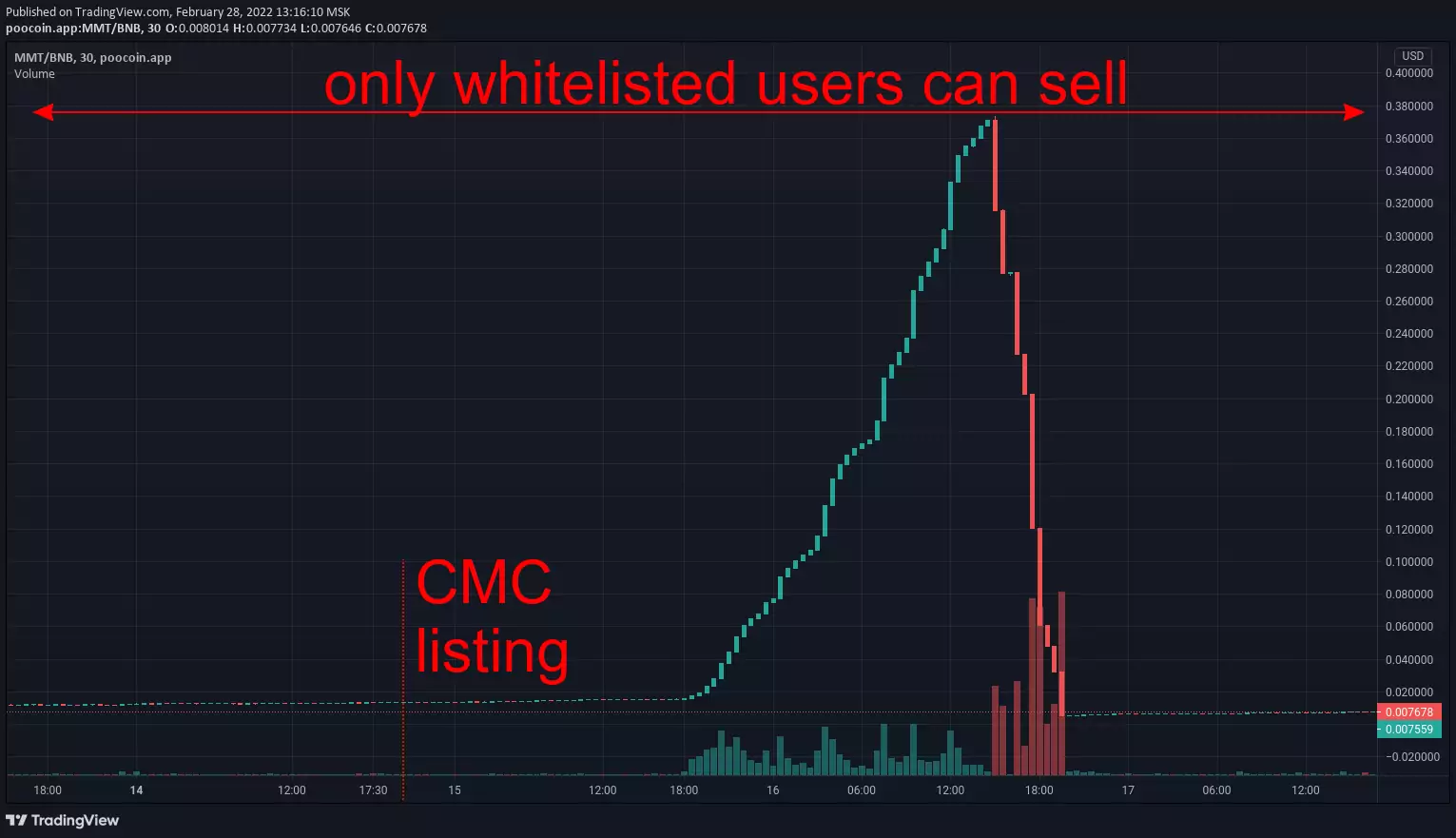
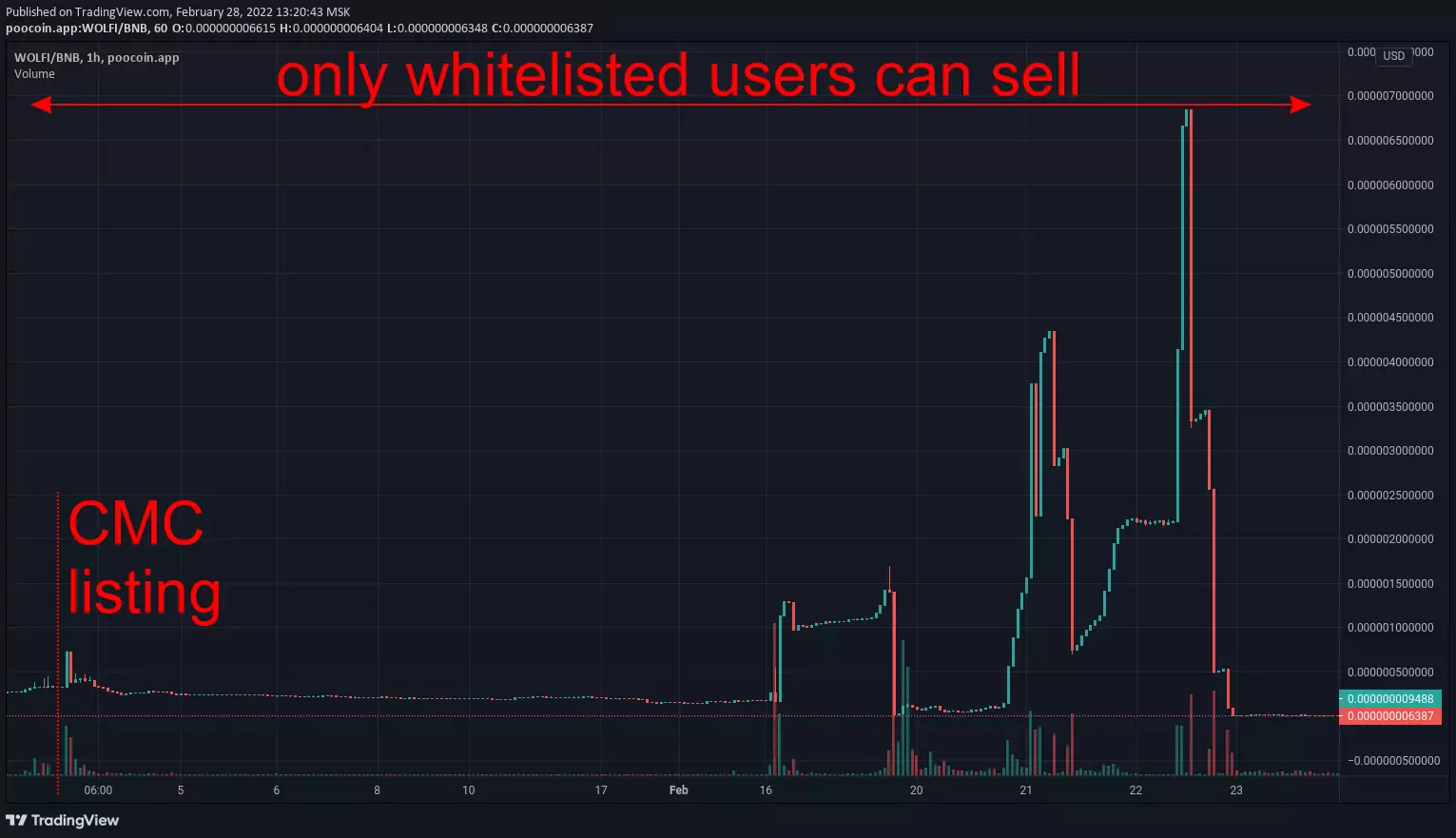
The idea is to trick you into buying a token that you won't be able to sell:
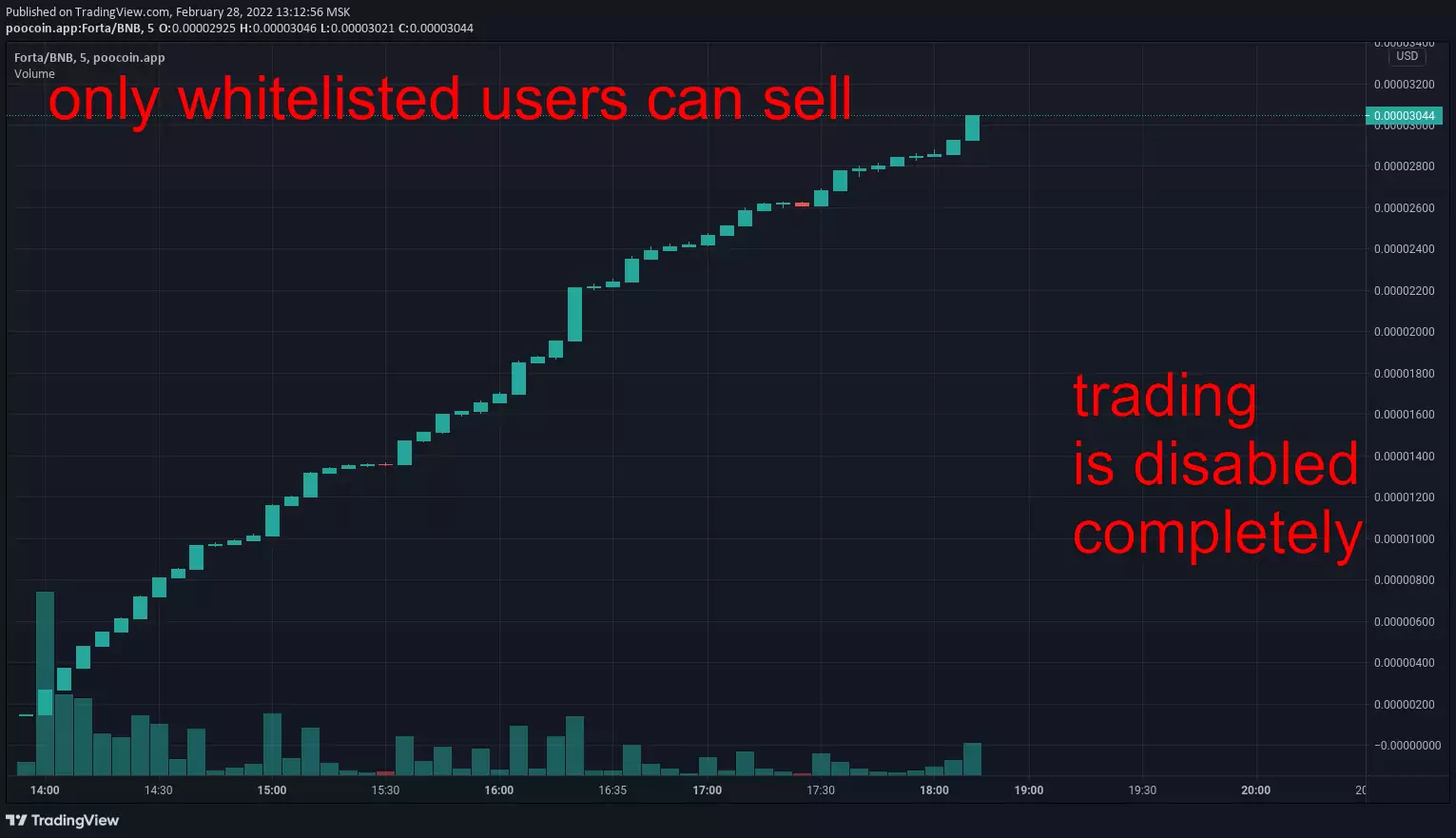
- trading honeypot — scammer can disable trading: via blacklists, pause/unpause, near-zero max transaction amount or any other method (illustration by PeckShield)
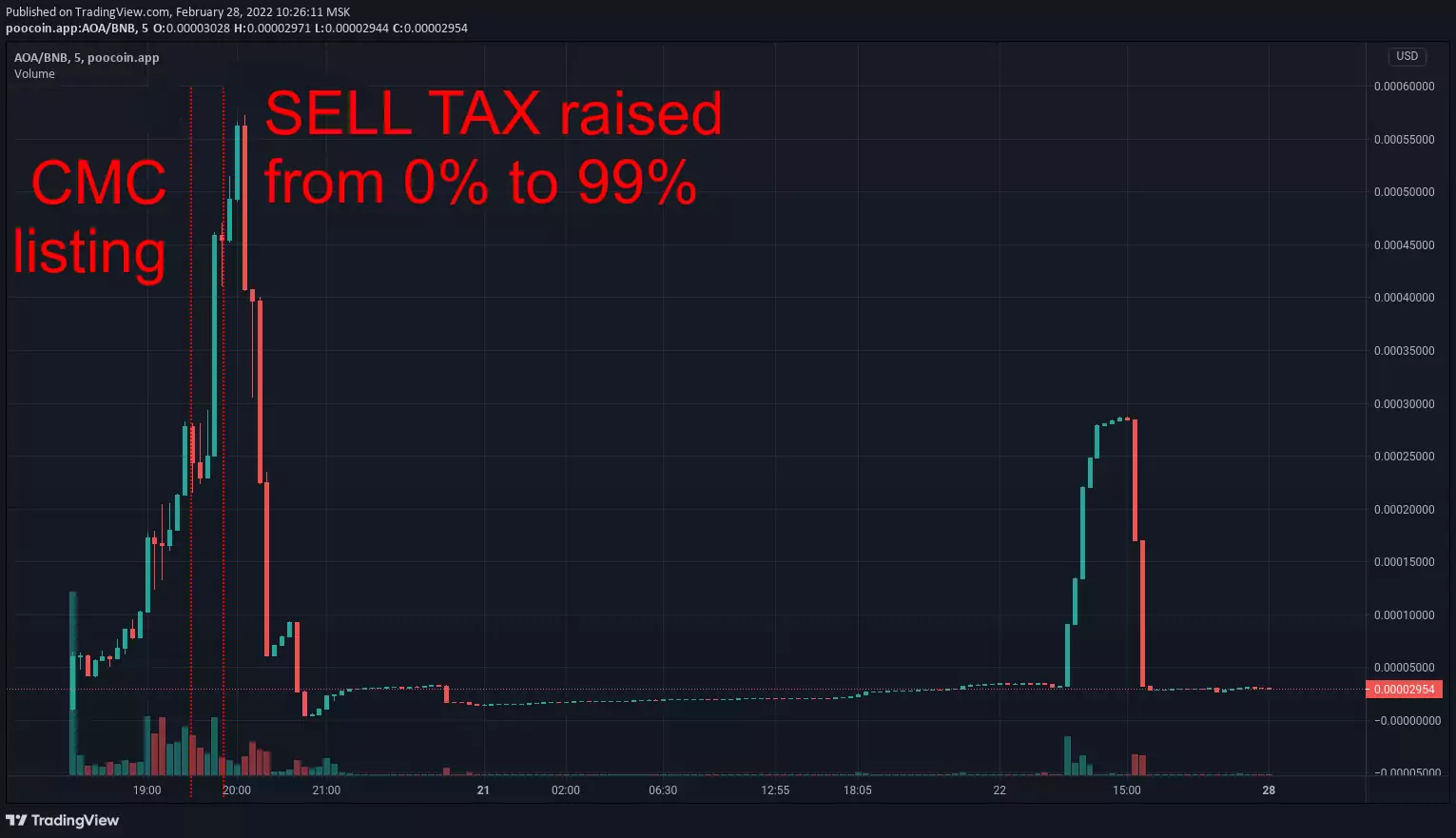
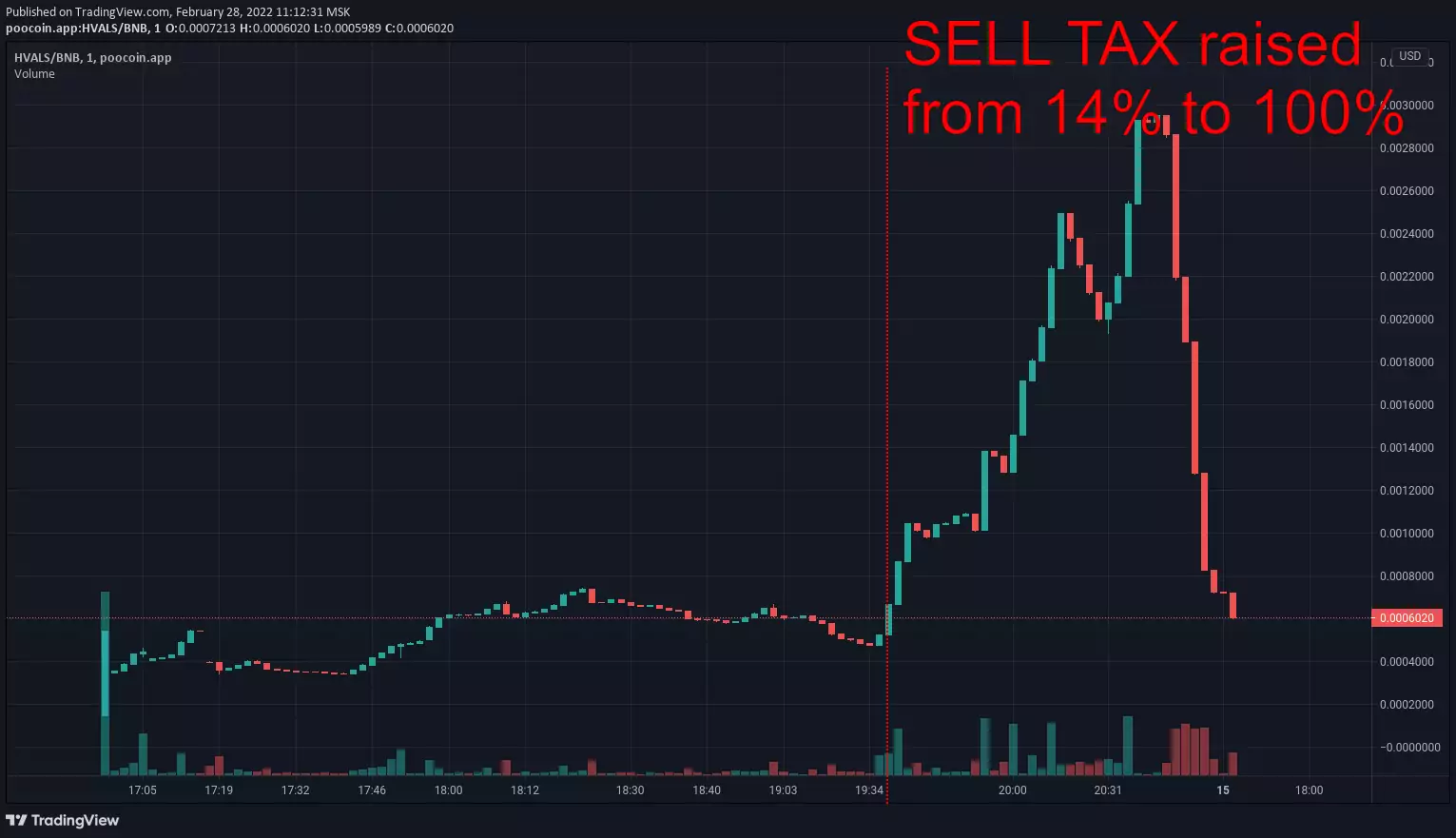
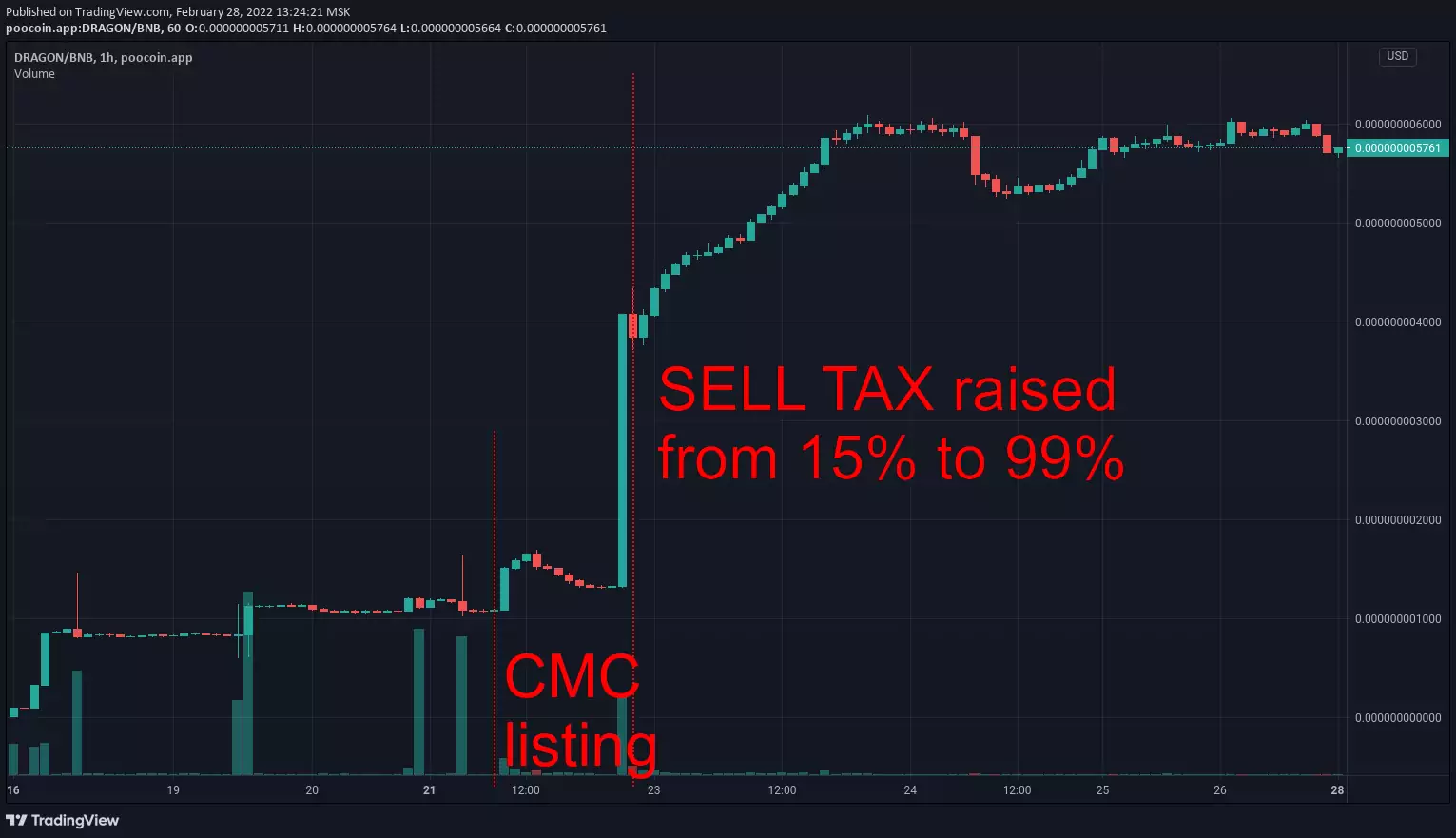
- tax honeypot — scammer can increase tax rate to an extreme level (e.g. 90%): you "can" sell but all your investments will be collected through taxes to a scammer-controlled address
- buyback honeypot — scammer can reduce your token balance to 0: some tricky contract call initiates burn, transfer or other non-trading event which results in an abritrary change in the amount of token that you own
In every case scammer abuses your inability to sell. Your money get stuck in liquidity pool which makes it a "honeypot". When enough money are collected scammer pulls them out and runs away with all the "honey".
Indentification
Honeypot tokens:
- always are immature projects: they never have major CEX listings, working services, reputable audit, often are anonymous, etc.
- often have non-existent community: you either can't find social accounts or it is small / inactive / full of bots
- often have non-renounced ownership: manual control over the contract is suitable for tax adjustments, trading halts, fraudulent event initiation, etc.
- often have no reputable audit: scammers don't want auditors to warn you about malicious functions
- often have "green chart": price grows indefinitely with no substantial corrections
- often are similar to rug pulls: easiest way to drain collected liquidity is to rug pull it
Check taxes, renounced ownership, disabled trading using tokensniffer.com, honeypot.is, app.staysafu.org, rugdoc.io
Try to find contract audit and to read it. If it mentions that deployer can burn or lock user funds, pause the contract, change taxes, blacklist holders from trading, buyback tokens, etc. — then there is a high honeypot risk.
PeckShieldAlert Tweet: Pattern in recent honeypots
Mitigation
Your best strategy is to avoid buying potential honeypots.
If you've already invested in one — your money are probably gone forever. Just walk away.
Some honeypots are serial (e.g. NinjaFloki). Therefore it's important to make information about them public:
- press "report" button on token's page at desk.lsr.finance or write about scam in our telegram group: @Laser_Desk
- make twitter post referencing scam token, its contract address and twitter account
- report token to chainabuse.com (it's a multi-chain community platform supported by crypto giants - Binance, Solana, OpenSea, Aave, etc.
- leave comment on token's page at tokensniffer.com or at CryptoScamReport subreddit
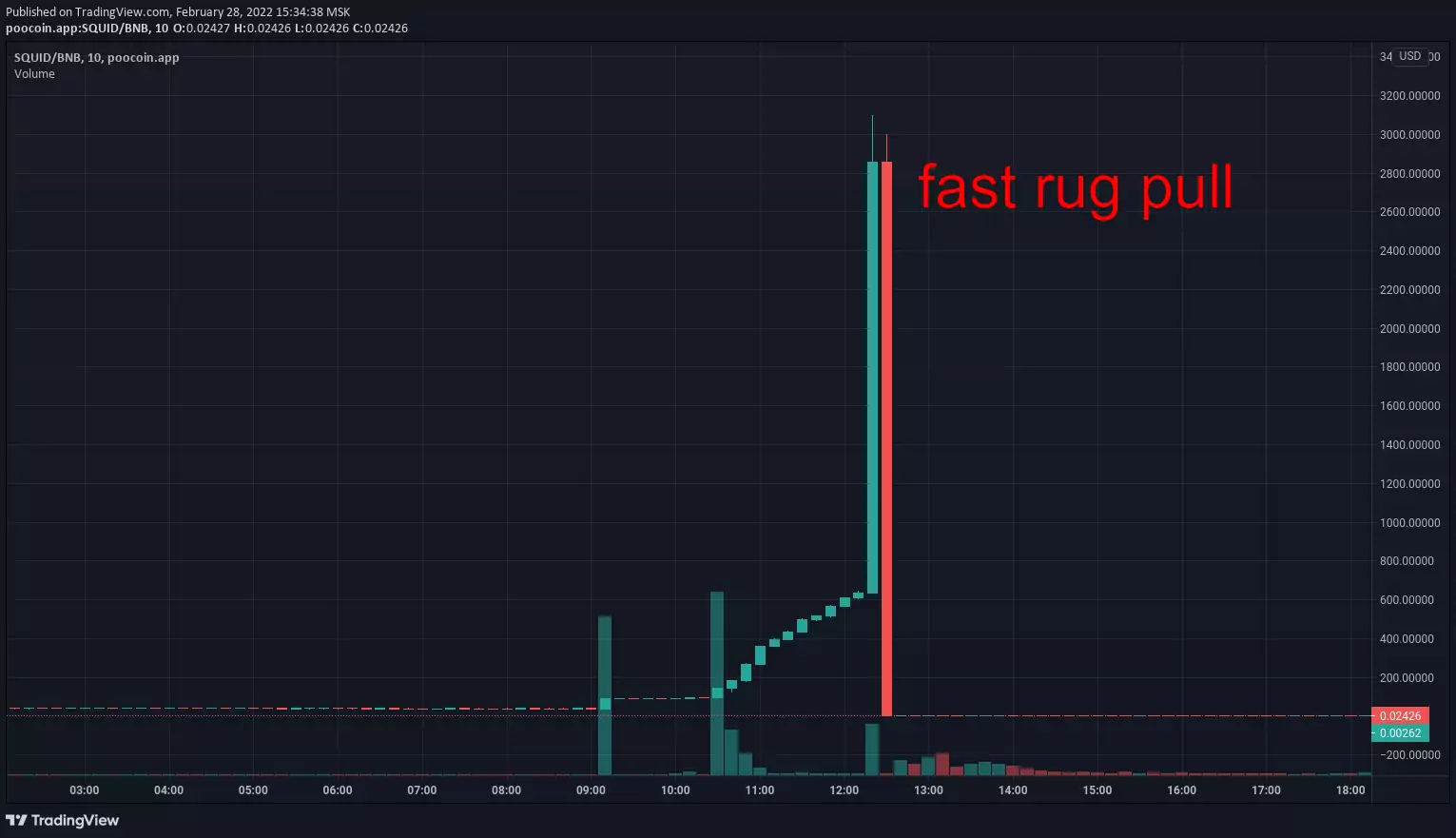
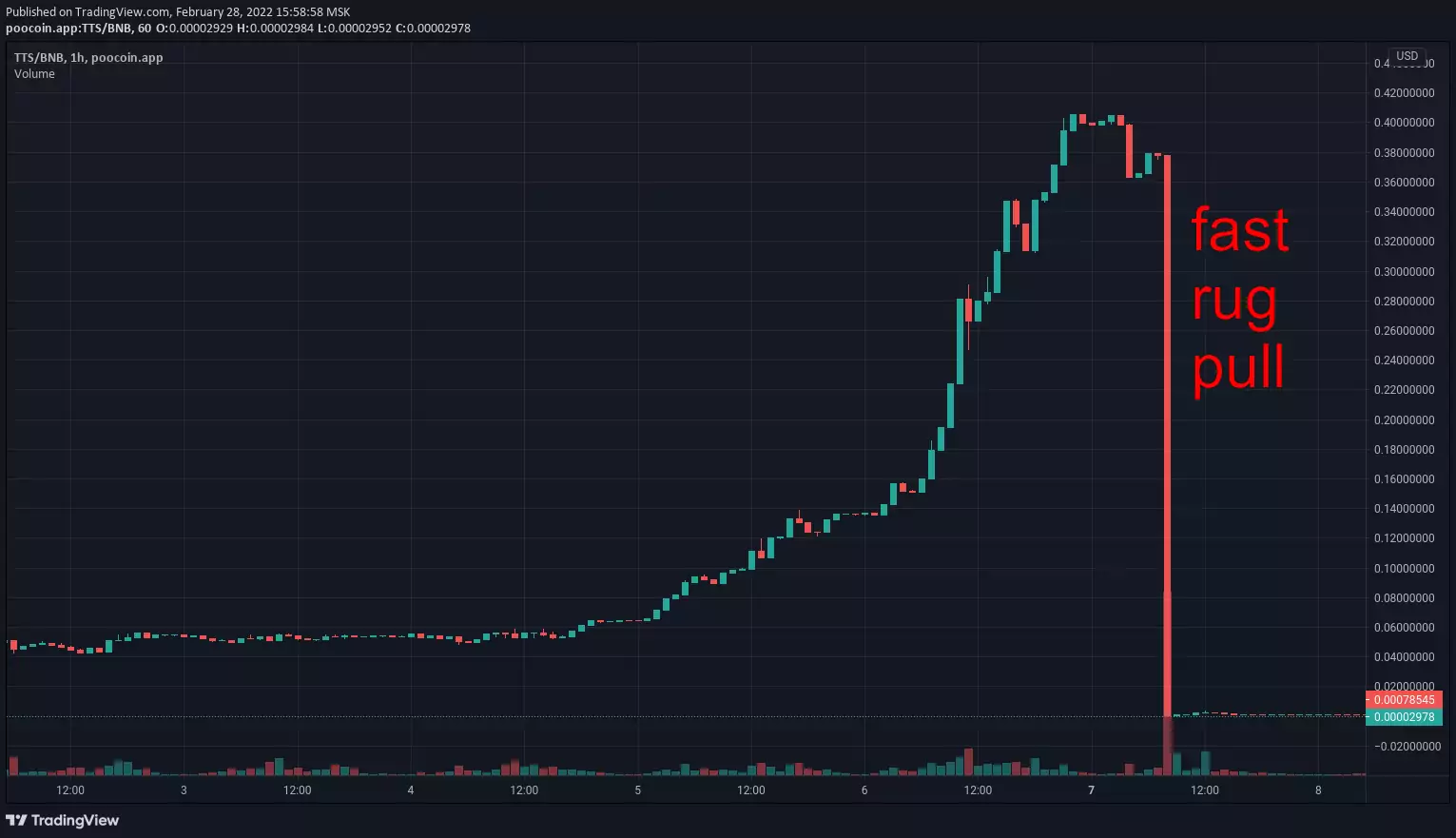
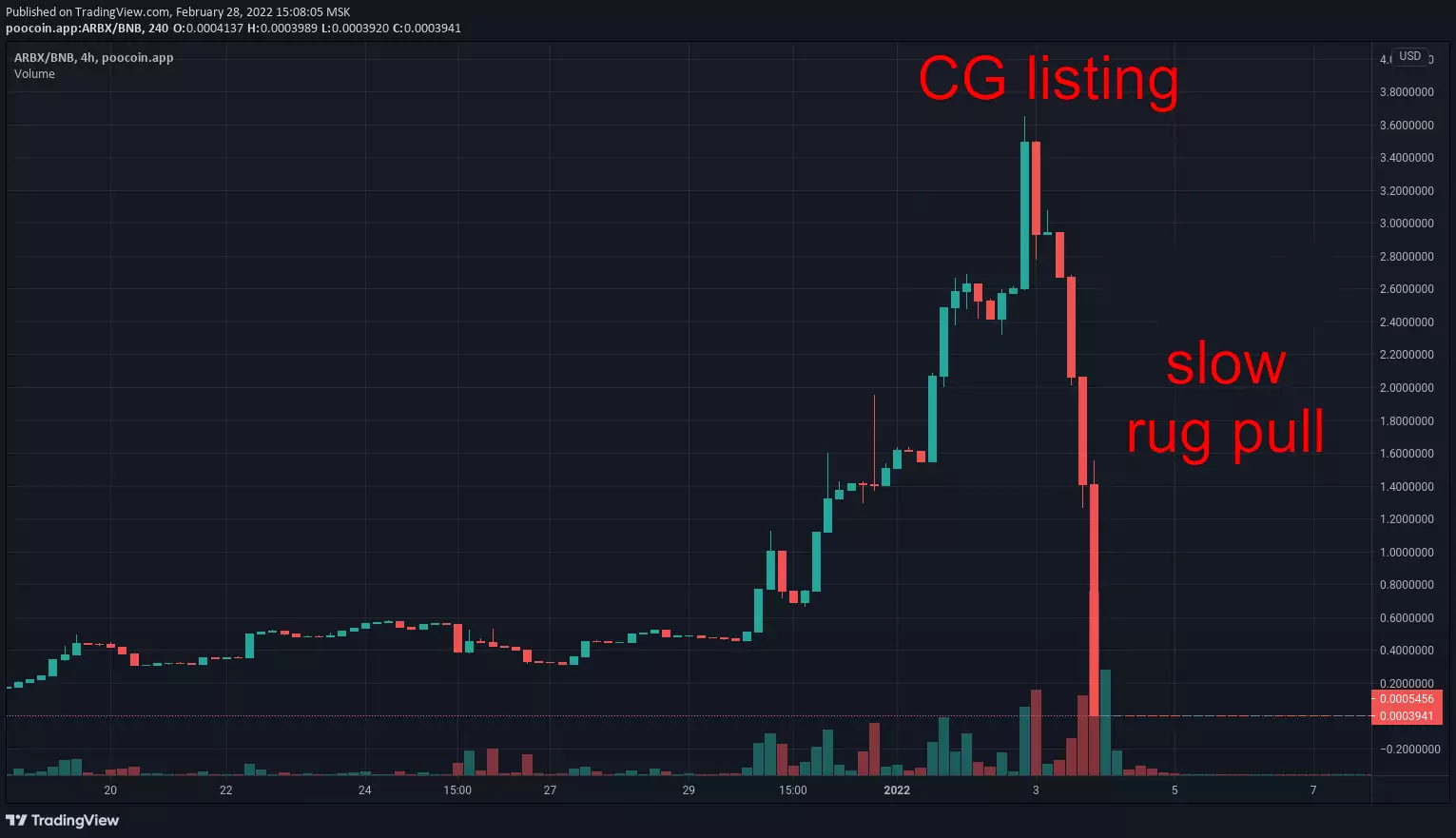
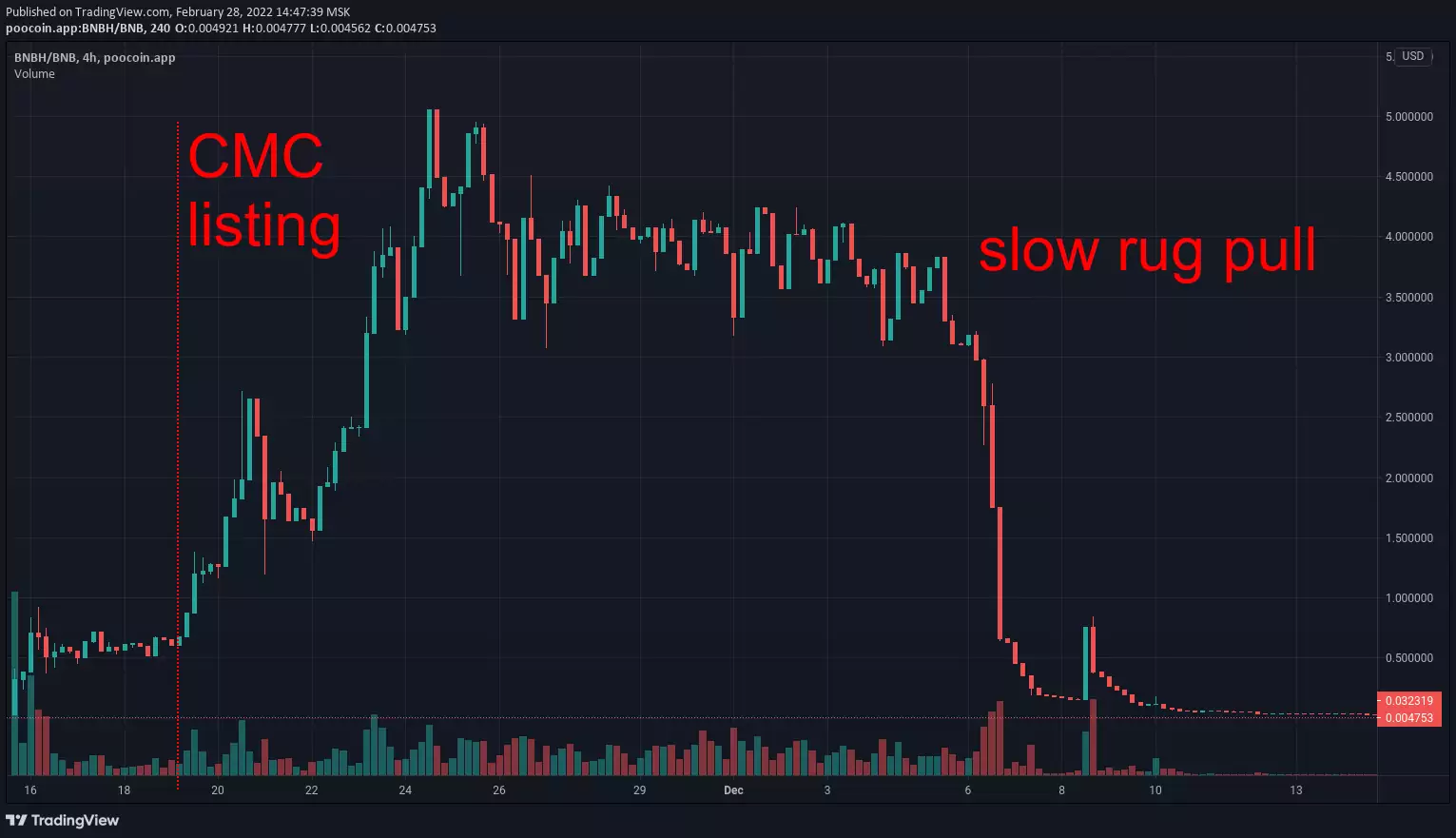
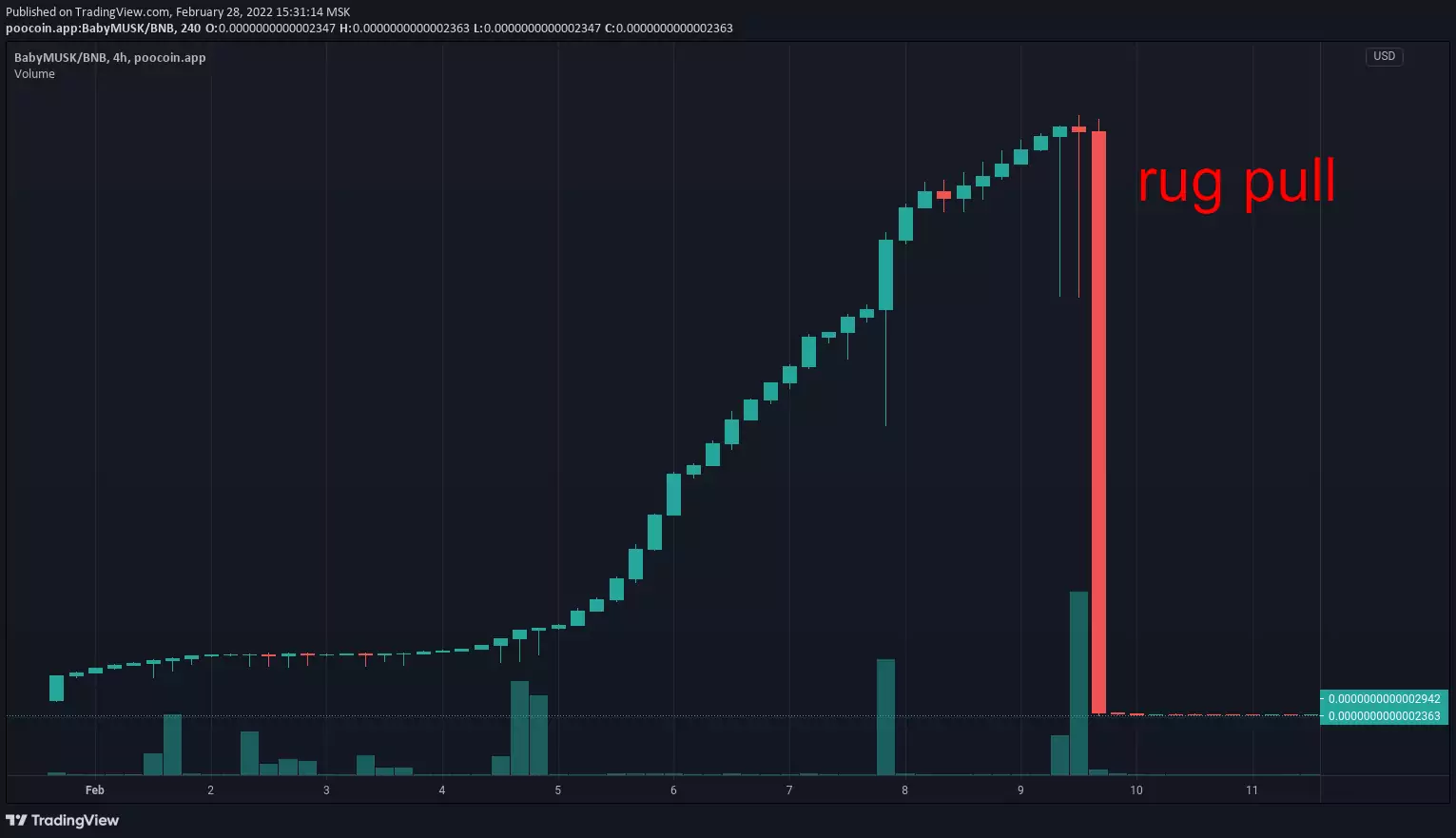
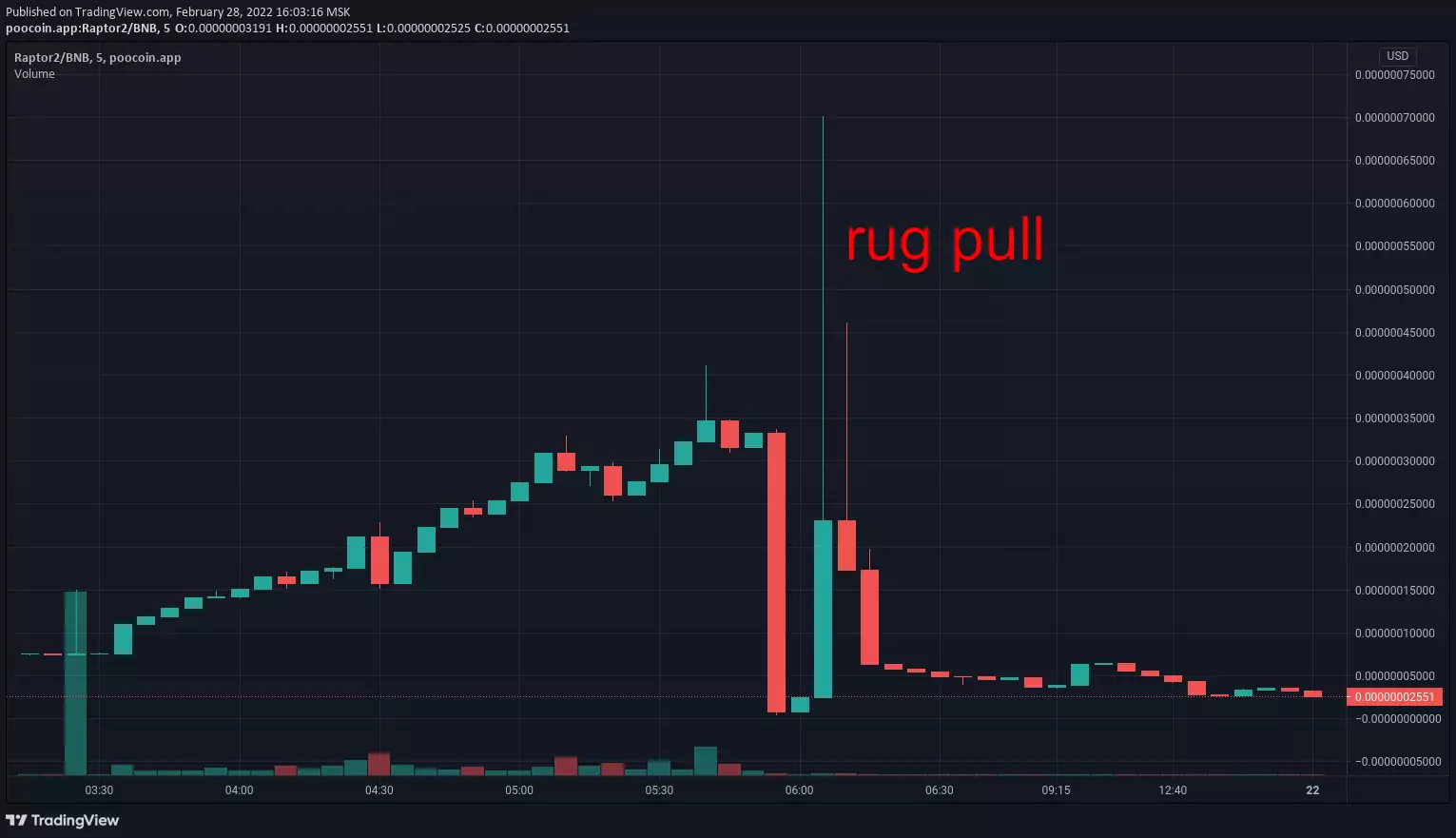
Examples of past scams: Squid Game, The third space, BNBHero, Arbix, BabyMUSK, Raptor2, ExoToken, PLATINX
Mechanics
The idea is to trick you into buying a token and then pull out the liquidity:
-
token rug pull — scammer sells a large amount of tokens: this sellout causes massive price dump and drains most of liquidity out of the pull
- fast rug — tokens are concentrated on few dev-owned wallets (classic rug pull): sellout happens in few transactions during a short period of time which causes a huge and immediate price drop
- slow rug — tokens are distributed across many dev-owned wallets: sellout happens in thousands of small transactions during a long period of time; it is discrete and may hard to notice from the price chart
- pool rug pull — scammer withdraws liquidity from the pool: price remains the same but no one is able to sell at this price because there are no money left in the pool
Sometimes rug pull happens due to a hack. For example, scammer can gain access to a dev wallet and dump corresponding tokens to the market (e.g. ARIVA hack). Other common hack is a flash loan (article 1, article 2).
Indentification
Rug pulled tokens:
- often are immature projects: they never have major CEX exchange listings, never have a working product, often are anonymous, etc.
- often have unlocked/unburned liquidity: this allows scammer to withdraw it
- often have big (relative to the pool) dev-controlled wallets: this allows scammer to drain out liquidity from the pool by selling his tokens
- usually produce a lot of hype and make agressive marketing: by usuing meme-related names and other tricks scammer aims to attract as many buyers as possible and as fast as possible
- sometimes have hidden mint functionality: this allows scammer to pass anti-scam checks and then rug pull liquidity by minting required amount of tokens
Check liquidity locks/burns, mint functions, holder concentration using tokensniffer.com, app.staysafu.org.
Articles:
- Koinly: Rug Pulls: Your Complete Guide
- CertiK: What Is a Rugpull? Tips on How To Avoid Them
- CertiK: What is a Soft Rugpull vs a Hard Rugpull?
- StaySAFU: What is a rug pull and how to avoid it?
Mitigation
The safest strategy is to avoid holding rug pullable token.
Contrary to honeypot it is always sellable. This makes you the master of your fate.
If you are unsure about some token — just sell it. Don't follow your FOMO and greed. They will make you hesitate for too long. There is no way to get your money back after the rug.
If team announces that rug pull was caused by a hack — just wait. In many cases projects recover or compensate losses.
Fakes
-
fake token — scammer chooses some legit token and makes new one with similar name / symbol
- DogeKing has many clones with exactly the same name and ticker: clone 1, clone 2, clone 3, clone 4, ...
- MetaSoccer from Polygon chain has a fake BSC token "Meta Soccer-0xe8377a076adabb3f9838afb77bee96eac101ffb1" which is a honeypot. Adding contract name to a token name is a clever trick than makes scam token appear in Poocoin search and fool unsuspecting investors.
- Yetiswap from Avalanche C-chain has a closely-named fake BSC token: yetiswap.io, which is a phishing (fake airdrop) scam.
- fake giveaway — scammer impersonates some celebrity and claims to give away crypto: participation requires sending some crypto to an advertised address — ofc it will be stolen and giveaway will never happen (article: Fake giveaway scams and how to avoid them (Reddit link), Medium link)
- ponzi scheme — scammer pays high rewards out of invested money; eventually investments stop and the whole pyramid collapses (e.g. Baked Beans)
- pump & dump — holders of a low-value asset promote and “talk it up” to encourage others to buy and increase its price. When the price reaches a certain point, the orchestrators of the scheme sell, take their profits and fade away before the price drops, with later investors left holding the bag. (article: Pump-and-Dump Schemes in Crypto
Fakes are designed for inattentive investors. To avoid them — ALWAYS double-check information at official website or in official social accounts.
Dangerous risks
- blacklist — token has been created by a developer blacklisted for past scams
- dead — project is not maintained: social accounts are dead or unmoderated, there are no news, there is no working service, etc.
- rebase (elastic supply) — price affects token supply: these tokens have complex mechanics and appealing ever-growing chart. Sometimes they are scams (PumpETH) and sometimes they are not. But in any case they require a clever investment approach. We advice all unsophisticated investors to skip rebase tokens.
Sometimes scams are hard to classify. In this case we mark them as unclassified scam.
Sometimes scam has yet to reveal itself. But transactions and / or social accounts are already unnatural (generated by bots). In this case we mark token as potential scam.